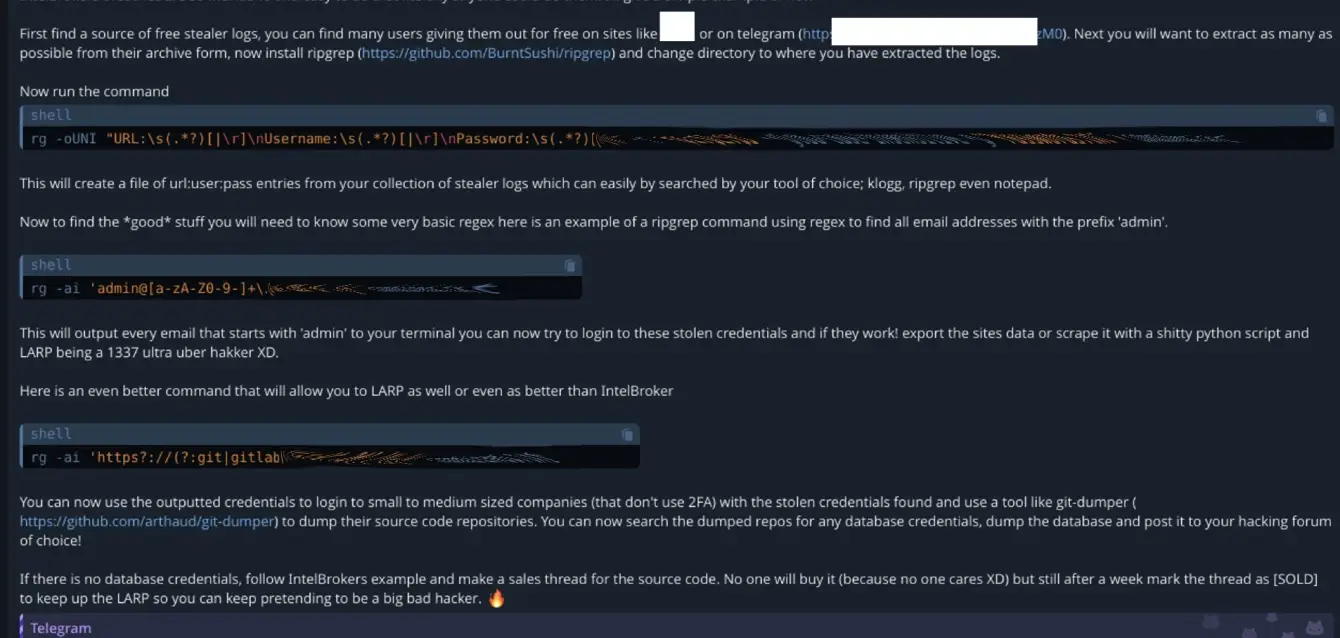
Recently, we came across an alarming discussion in a Telegram group dedicated to trading stolen credentials and other fraudulent activities. In this conversation, one member shared a practical tutorial on how to replicate techniques used by the well-known IntelBrokers cybercrime operation, highlighting how easily individuals, even without significant technical skills, can perform similar attacks.
Common Tools in Wrong Hands
The tutorial focuses on using ripgrep (rg), a tool normally used by developers and administrators for efficient searches in large volumes of text. However, when used maliciously, this tool becomes a powerful means of extracting sensitive credentials, such as logins and passwords, from stolen logs (credentials). The simplicity of the commands presented in the conversation demonstrates that practically anyone can use these techniques to compromise systems and access private information.
The Path to Fraud
The conversation suggests that after extracting credentials, fraudsters can use them to access small and medium-sized business accounts, which often don’t implement two-factor authentication (2FA). Tools like git-dumper are mentioned for stealing source code repositories, which may contain more credentials and secrets. Additionally, the group encourages the practice of posing as a “professional hacker” when selling this material on cybercrime forums, even if the obtained value is minimal.
The Concerning Reality
This example highlights a worrying issue: the ease with which cybercriminals can leverage legitimate and public tools for illicit purposes. The accessibility of these tools, combined with companies’ lack of awareness and adequate security, creates fertile ground for attacks that can result in serious financial and reputational damage.
Saturated Market
One aspect that stands out in the group conversation is how criminals describe the sale of stolen data. Almost comically, the author suggests that after obtaining credentials and victim information, it’s possible to “open a sales thread” on cybercrime forums, similar to practices seen by IntelBrokers. However, he admits that often nobody cares about this data, given the volume of stolen information available on the dark web.
The irony in the message highlights a scenario where cybercriminals themselves acknowledge the saturation of the stolen data market. This, however, doesn’t diminish the gravity of the situation. Even if selling certain information isn’t profitable, the exposure of sensitive data in public or private environments still represents a significant threat to individuals and organizations.
The process of creating a sales thread on forums, even if just to “maintain the hacker pose,” reveals how criminals not only profit but also build reputations in their communities. These reputations are often used to promote future sales, increase credibility among them, or even recruit new members to their criminal networks.
Conclusion
This practice reflects a dark side of even the stolen data market, where, even if the information has no commercial value, its public exposure can still cause irreparable damage. For companies, the lesson is clear: each exposed dataset, no matter how insignificant it may seem, can be used in ways that go far beyond simple sales. This reinforces the importance of robust security and constant vigilance to prevent sensitive information from falling into the wrong hands.
It is fundamental that organizations continuously review their security practices and adopt proactive measures, such as two-factor authentication and constant auditing of logs and accesses. Additionally, education about cyber threats and promotion of good security practices are essential to mitigate risks and protect sensitive information from being exploited by criminals.