User USDoD posted on the cybercrime forum BreachForums claiming to have obtained what they alleged to be “the entire threat actor list” from CrowdStrike. The user also claimed to possess “the entire IOC [Indicators of Compromise] list” from CrowdStrike and stated they would release it “soon.” To support their claim, USDoD provided a download link for the alleged threat actor list and shared sample data fields.

The CSV file contains data on 245 threat actors that are relatively public. According to USDoD, this data was obtained through a technique called scraping, which involves extracting publicly available information from websites. USDoD stated that they used this technique on CrowdStrike’s official website, suggesting that the data wasn’t stolen in a traditional manner but rather collected from a publicly accessible source.
However, it’s important to note that access to this information may have been facilitated by the use of leaked credentials obtained via “stealers.” Stealers are types of malware designed to steal sensitive information from infected systems, including login credentials and financial data. In this context, it’s possible that USDoD used stolen credentials to access a restricted section of CrowdStrike’s website where this data was available, and then performed the scraping.
For more details about the mentioned content or to learn how to protect against data leaks through Stealers, contact our team of specialists, who are ready to provide personalized guidance and support.
Regarding the claim of having a list of 250 million Indicators of Compromise (IoCs), this could represent a more significant and sensitive data leak. IoCs are information used to identify possible malicious activities in IT systems, such as malicious IP addresses, suspicious domains, or malware signatures. If this IoC list is legitimate and indeed from CrowdStrike, it could include critical information for the cybersecurity of many organizations, making it a valuable asset for attackers.
Additionally, USDoD claimed to have obtained “two large databases from an oil company and a pharmaceutical industry (not from the US).” It wasn’t clear if these claims were related to the alleged CrowdStrike data leak.
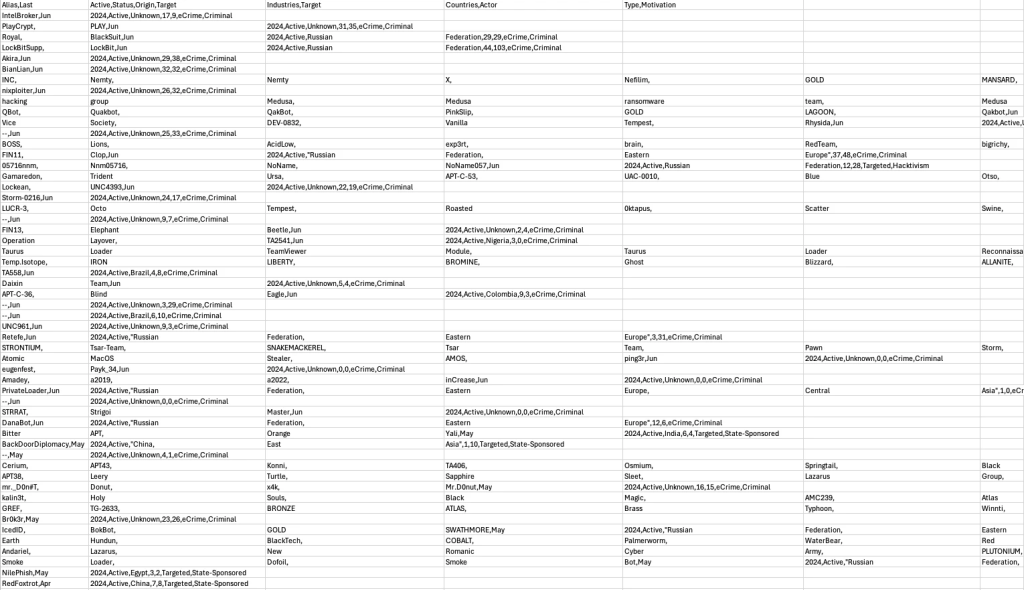
The CSV file contains detailed information about various cyber threat entities, including aliases, activity status, origins, target industries and countries, actor type, and motivation. Analysis of the content reveals the following:
Diversity of Actors and Origins: The file lists a wide variety of cyber actors, with geographic origins predominantly in the Russian Federation, Eastern Europe, China, and Iran. Actors from Brazil, Colombia, and other countries are also mentioned.
Motivations and Types of Activities: The actors’ motivations vary between cybercrime, hacktivism, and state-sponsored activities. Many groups are involved in targeted intrusion campaigns, often motivated by political or economic reasons.
Target Industries and Countries: The data indicates that targets include a wide range of industries and countries, with some actors focusing on multiple sectors and regions. This reflects the diversified strategy and global reach of many of these threats.
Activity Status: Most of the listed groups are active as of June 2024, with some groups identified as inactive or retired. This suggests a constant evolution of the threat landscape, with groups emerging, transforming, or disappearing over time.
Group Specifics: The file details the operations and characteristics of various groups, such as the use of multiple aliases, associations with known campaigns, and specific attack techniques.
More Information About Hacker USDoD
USDoD has a history of making exaggerated claims, likely to enhance their reputation in hacktivist and cybercrime circles. In the past, they claimed to have conducted a hack-and-leak operation targeting a professional networking platform, but industry sources debunked these claims, stating that the data was obtained through web scraping rather than a targeted breach, similar to what happened now with the CrowdStrike website.
Since at least 2020, USDoD has been involved in both hacktivist and financially motivated breaches, primarily using social engineering tactics to access sensitive data. In the last two years, the user’s focus has shifted to intrusion campaigns. Since January 2024, USDoD has been seeking to diversify and expand their cyber activities, including administering cybercrime forums.
More recently, USDoD claimed to have breached Thales, a major defense organization, and shared sample data to corroborate this claim, although it hasn’t been officially confirmed yet. The user operates with a humorous approach and, in a recent interview with DataBreaches, revealed details about their identity, including their age, nationality, and alleged connections with high-ranking officials in Spain.
The hacker, who is in their 30s, confirmed they are not of Russian origin and emphasized that they operate independently, without association with ransomware groups. Originally from South America but currently residing in Portugal, they mentioned: “English is not my primary language,” according to DataBreaches.
In mid-May this year, in one of BreachForums’ private channels, one of the members mentioned that USDoD was of Brazilian nationality. In response, USDoD marked the comment with a “secret” emoji, fueling speculation about their true origin.
Previously, the hacker leaked sensitive information about approximately 3,200 Airbus suppliers on BreachForums, claiming to have acquired this data through stolen passwords from an employee of a Turkish airline with access to Airbus systems.