Stay ahead of credential theft with real-time identity monitoring
Our Identity Intelligence solution empowers organizations to maintain comprehensive control over their digital identities and credentials across the threat landscape. With real-time monitoring capabilities, organizations can proactively detect and respond to potential credential exposures before they escalate into security incidents.
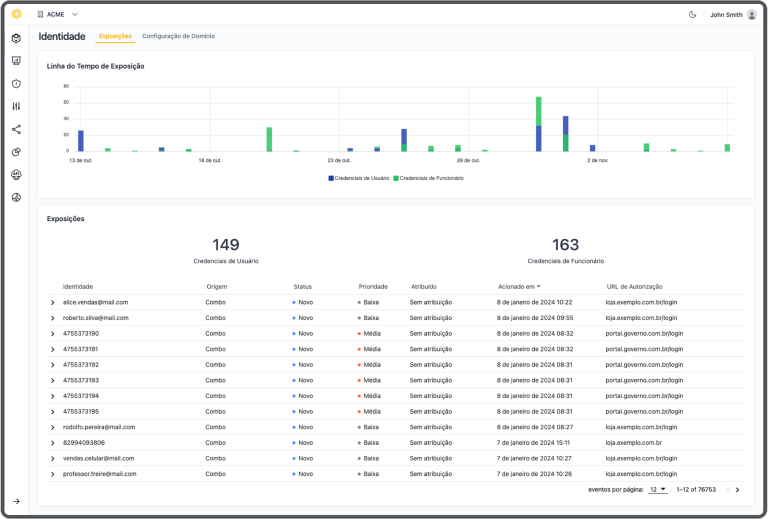
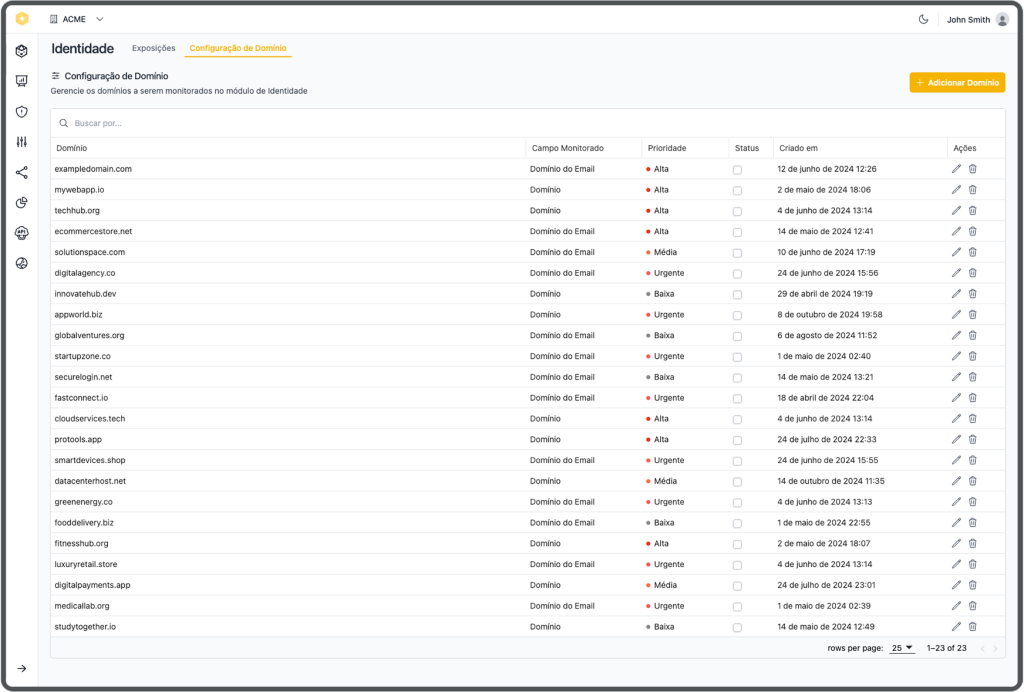
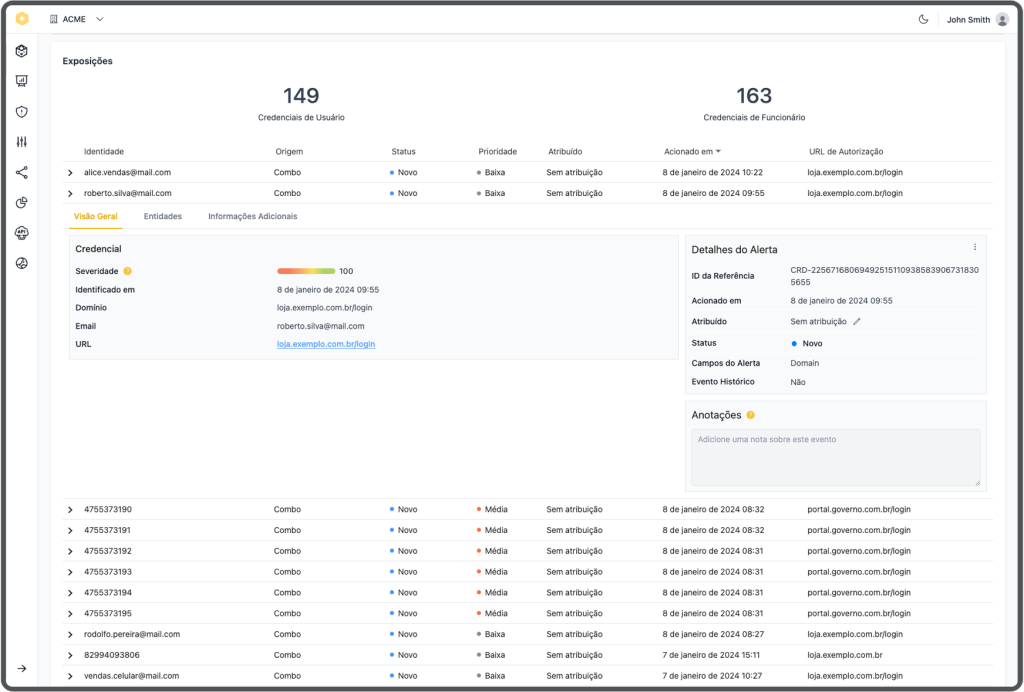
The platform provides deep visibility into both user and employee credential exposures through an intuitive interface that tracks compromised identities across various domains. Organizations can efficiently monitor multiple domains simultaneously, with customizable priority levels and automated alerts for immediate action when credentials are exposed.
Advanced analytics and trending data help security teams understand exposure patterns over time, enabling them to identify potential security gaps and strengthen their overall security posture. The detailed event timeline shows exactly when and where credentials were exposed, while the severity scoring system helps teams prioritize their response efforts effectively.
Key capabilities:
- Infostealer monitoring
- Lookup for compromised credentials
- Integrations and API
Infostealer Monitoring: Actively detect and track credentials stolen by malware in real-time. Our platform continuously monitors infostealer logs and data dumps, providing immediate alerts when your organization’s credentials are identified in malware campaigns. This early warning system enables rapid response to potential compromises before attackers can exploit stolen credentials.
Lookup for Compromised Credentials: Instantly verify if any corporate credentials have been exposed in data breaches or are being traded on the dark web. Our comprehensive database constantly updates with newly discovered credential leaks, allowing security teams to proactively identify compromised accounts and take immediate action to prevent unauthorized access to corporate resources.
Integrations and API: Seamlessly incorporate credential monitoring into your existing security infrastructure through our flexible API and pre-built integrations. Connect with popular SIEM platforms, identity providers, and security tools to automate credential verification and incident response workflows. Our REST API enables custom integration development, allowing organizations to build automated remediation processes and enhance their security operations efficiency.
Through our comprehensive credential monitoring system, we maintain vigilance over a massive database exceeding 20 billion unique credentials. Our platform processes more than 250,000 new credentials daily, collected from various sources including data leaks, dark web marketplaces, and infostealer logs. This unparalleled coverage ensures your organization's digital identities are continuously protected against emerging threats and potential compromises.
Extensive Credential Intelligence Coverage
how it worksFrequently Asked Questions
Organizations need Identity Intelligence to proactively protect against unauthorized access resulting from compromised credentials. With the increasing frequency of data breaches and credential theft, continuous monitoring of exposed credentials becomes crucial to prevent account takeover attacks and maintain robust security posture.
Infostealer logs provide real-time intelligence about newly compromised credentials, often before they appear in dark web dumps. This early detection capability gives organizations a critical time advantage to respond and prevent credential abuse before attackers can exploit them.
Identity Intelligence offers seamless integration with SIEM platforms for centralized security monitoring, email notifications for instant alerts, CyberArk for privileged access management, and a comprehensive REST API for custom integrations and automated workflows.